- DDoS
- Arbor Networks - DDoS Experts
2024 DDoS-for-Hire Landscape Part 1
An Introduction

Executive Summary
The DDoS-for-hire industry has transformed drastically in recent years, marked by innovations in automation, more accessible reconnaissance tools, and even the early adoption of artificial intelligence (AI). These developments have lowered the barrier to launching complex DDoS attacks, making them more accessible to attackers of all skill levels. The rise of these services represents a significant shift in the cybersecurity landscape, pushing organizations to rethink and strengthen their defense strategies. In this first installment of a seven-part blog series, we break down how DDoS-for-hire platforms work, their expanding capabilities, and what this means for modern cyber defense.
What are DDoS-for-Hire Services?
DDoS-for-hire services, known in many circles as "booter" or "stresser" platforms, let users rent access to networks of compromised devices to execute DDoS attacks. These platforms are designed to be user-friendly, making it simple for anyone—even those without technical expertise—to launch substantial attacks against targets of their choosing. Despite their claims of being legitimate tools meant for stress-testing personal networks; these services are often misused for malicious purposes.
How Do These Services Operate?
Booter services present themselves as legitimate by advertising their features on forums, Telegram channels, social media, and even GitHub repositories. The process of getting started is intentionally straightforward: users can often access these services without needing to create an account or verify their email. This simplicity has opened the door for a wider range of attackers, beyond the state-sponsored entities and experienced cybercriminal groups, to carry out DDoS attacks with ease.
Growth and Promotion
The popularity of DDoS-for-hire services has grown significantly due to their aggressive promotion. Operators use every available channel to showcase their tools’ capabilities, from flashy advertising on underground forums to demonstrations on public social media channels. These platforms now cater not only to one-off, low-scale attacks but can launch persistent, automated attack campaigns that can take down entire infrastructures.
Figures 1 and 2 illustrate typical examples of how these services are promoted and advertised, showing their Terms of Service and a compilation of booter platforms available for potential users.

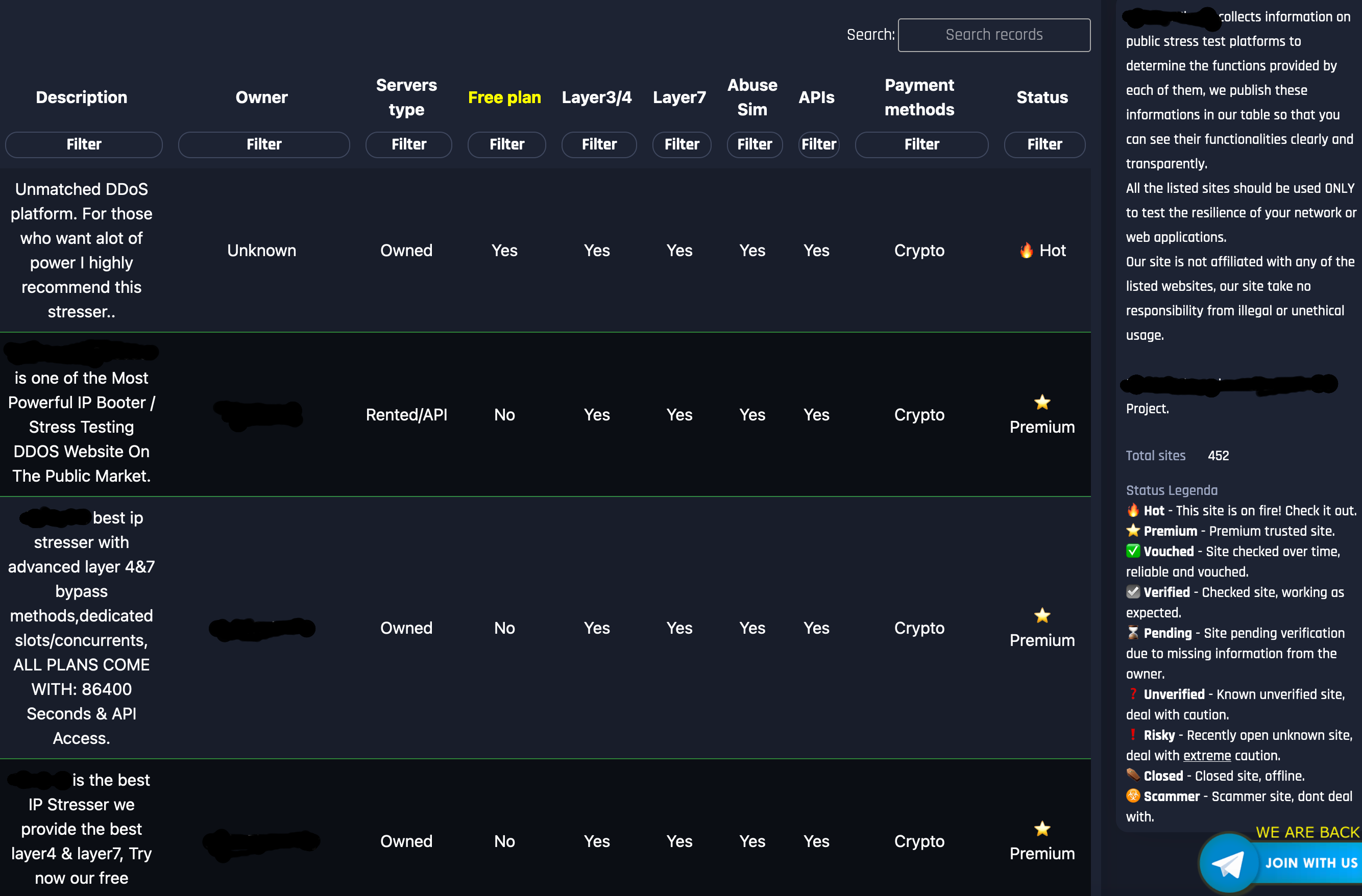
The Range of Services Offered
DDoS-for-hire platforms have come a long way from merely offering simple traffic-flooding tools. Now, they come equipped with:
- Pre-Attack Reconnaissance Tools: Attackers can identify vulnerabilities in a target network with minimal effort.
- API Integrations: These make it possible for attackers to seamlessly integrate DDoS capabilities into custom attack toolkits.
- Automated Scheduling: Users can plan and execute attacks that are fine-tuned for maximum disruption.
These features, which once required advanced technical skills to implement, are now available at the click of a button, opening DDoS capabilities to a broader pool of malicious actors.
The Evolution Over Three Years
In just three years, DDoS-for-hire services have evolved dramatically. Automation has revolutionized how these attacks are carried out. Previously, attackers had to oversee and manage the timing and parameters of their campaigns manually. Now, they can schedule, optimize, and even automate their attacks to repeat at regular intervals—all without ongoing human input.
The Threat to Organizations
For organizations, the increasing sophistication of DDoS-for-hire services poses a more formidable threat. With built-in reconnaissance tools, attackers can pinpoint weaknesses in a network and tailor their campaigns for maximum impact. These automated features and AI-driven capabilities push traditional defensive measures to their limits, necessitating advanced strategies for detection and mitigation.
Challenges in Detection and Defense
The accessibility and ease of these services mean that a broader range of attackers—hacktivists, cybercriminals, or opportunistic actors—can launch sophisticated DDoS attacks. The combination of automation and AI makes many traditional defenses obsolete, as these new capabilities allow attacks to adapt in real-time, sidestepping conventional protective measures like rate-limiting.
The Impact on Cybersecurity Strategies
For decision-makers, understanding how DDoS-for-hire services have evolved is crucial. The potential disruption from such attacks is significant, impacting everything from customer trust and revenue to the operational continuity of an organization. This evolving threat landscape demands cybersecurity strategies that go beyond reactive measures, emphasizing adaptive, intelligence-driven DDoS protection.
The Role of NETSCOUT
Despite the increasing complexity of DDoS-for-hire services, organizations can maintain a strong defense with the right solutions in place. NETSCOUT’s Adaptive DDoS Protection and ATLAS Intelligence Feed provide real-time, internet-scale insights that can adapt to the most sophisticated DDoS threats. By leveraging these comprehensive defense mechanisms, organizations can detect, mitigate, and neutralize even minute-zero attacks, ensuring operational resilience and continuity in an increasingly challenging cyber environment.
Continue reading in part two of our seven-part series: Pre-Attack Reconnaissance (Publishing on December 5, 2024)
- Arbor Networks - DDoS Experts
- Attacks and DDoS Attacks
- DDoS Tools and Services