- Arbor Networks - DDoS Experts
- DDoS
2024 DDoS-for-Hire Landscape Part 2
Pre-Attack Reconnaissance

Executive Summary
The proliferation of pre-attack reconnaissance tools embedded in DDoS-for-hire services has changed the nature of threat preparation. Once reserved for highly skilled adversaries, these capabilities are now available to attackers of all technical levels. This section explores the essential reconnaissance strategies used by threat actors, their implications for enterprise security, and how organizations can protect themselves against this evolving threat landscape.
The Role of Pre-Attack Reconnaissance
Pre-attack reconnaissance is crucial for attackers aiming to maximize the impact of a DDoS campaign. By analyzing a target’s network and understanding its defenses, attackers can select the most effective tactics. The streamlined integration of reconnaissance tools into DDoS-for-hire platforms has democratized this once-specialized phase, reducing the expertise needed to gather actionable intelligence.
Key Capabilities of Reconnaissance Tools
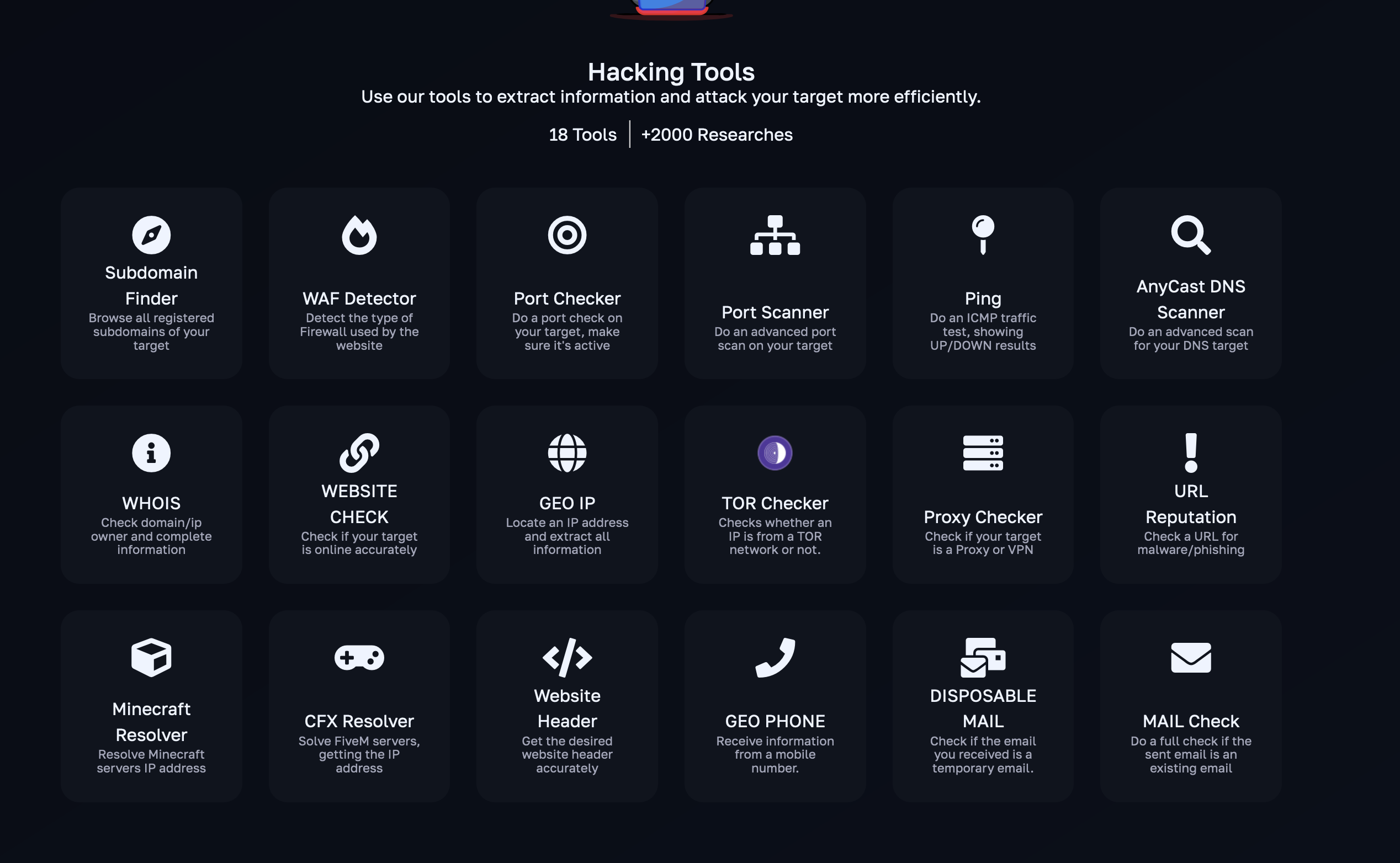
Modern DDoS-for-hire services now include integrated reconnaissance functionalities that:
- Identify Network Weaknesses: Automated scanning tools reveal subdomains, DNS servers, and other critical network elements.
- Uncover Defensive Mechanisms: Attackers use these tools to find web application firewalls (WAFs) or open ports, providing insights into the types of attacks that would be most effective.
- Map Digital Assets: Comprehensive subdomain finders help adversaries prepare for large-scale attacks, such as carpet-bombing multiple web assets within a targets web server.
Implications for Organizations
The accessibility of these tools has significant consequences:
- Lowered Entry Barrier: The reduced skill requirement means a broader range of attackers, including low-skilled individuals, can initiate high-impact DDoS attacks.
- Quicker Attack Preparation: Automated reconnaissance enables attackers to plan and launch attacks rapidly, minimizing the window for defenders to respond.
- Increased Precision: The ability to map out network vulnerabilities in detail allows attackers to execute highly targeted and adaptive DDoS campaigns.
Real-World Impact
Recent examples demonstrate how reconnaissance enhances the effectiveness of DDoS campaigns:
- Corporate Network Attacks: During periods of increased remote work, attackers used port scanners and VPN detectors to identify and disrupt vital corporate resources.
- Broad-Scope Assaults: Hacktivist groups have employed subdomain mapping and website crawling to target multiple entry points under the same organization’s top-level domain, amplifying the reach and disruption of their attacks.
Challenges in Defense
Detecting reconnaissance activities poses unique challenges:
- Hidden in Legitimate Traffic: Reconnaissance can often resemble benign scanning or normal user behavior, making early detection difficult.
- Rapid Shifts: The dynamic nature of automated scanning means attackers can change their strategy quickly, bypassing traditional static defenses.
Leveraging NETSCOUT for Proactive Defense
To mitigate the risks posed by reconnaissance tools, organizations must adopt a proactive approach. NETSCOUT’s Adaptive DDoS Protection, paired with the ATLAS Intelligence Feed (AIF), enables early detection of reconnaissance efforts like scanning. This intelligence equips organizations with the foresight needed to bolster defenses before an attack begins, ensuring a robust response that disrupts attacker strategies and protects critical infrastructure.
Continue reading in part three of our seven-part series: API Usage (Publishing on December 10, 2024)
- Arbor Networks - DDoS Experts
- Attacks and DDoS Attacks
- DDoS Tools and Services
