- Arbor Networks - DDoS Experts
- DDoS
2024 DDoS-for-Hire Landscape Part 3
API Usage

Executive Summary
The incorporation of APIs into DDoS-for-hire services has revolutionized the ease with which attackers can plan, launch, and manage DDoS attacks. These APIs enable seamless integration into broader attack infrastructures, allowing for unprecedented levels of automation and control. This section explores how APIs have become a crucial component in the DDoS landscape, the impact on cybersecurity, and how organizations can defend against this evolving threat.
APIs and Their Role in DDoS-for-Hire Services
Application Programming Interfaces (APIs) are integral to modern technology, facilitating interaction between different software components. In the realm of DDoS-for-hire services, APIs allow attackers to enhance their capabilities by embedding these services into custom attack platforms. This capability enables:
- Remote Control and Coordination: Attackers can manage DDoS operations from anywhere, coordinating attacks without needing direct interaction with the service interface.
- Enhanced Efficiency: With simple API calls, attackers can automate and orchestrate complex attacks with speed and minimal manual input.
The result is an increase in both the frequency and complexity of attacks. API integration reduces the time from planning to execution, enabling attackers to strike with precision.
How APIs Enhance DDoS Threats
APIs offer attackers a range of powerful advantages. One significant benefit is the ability to automate attack scheduling, allowing threats to be launched at optimal times, such as during a target’s peak operational hours or when defenses are weakest. The flexibility of APIs means that an attacker can:
- Adapt on the fly by modifying attack parameters mid-campaign.
- Deploy multi-vector assaults seamlessly, targeting different parts of a network to evade detection.
- Moreover, APIs facilitate integration with other tools and botnets, creating a seamless ecosystem where various malicious activities are coordinated efficiently.
Examples of API Integration in DDoS Attacks
Real-world use cases illustrate the impact of API integration:
- Adaptive Attacks: Attackers can program APIs to adjust the rate and intensity of DDoS traffic in response to defensive measures like rate-limiting. This adaptability makes it challenging for traditional defenses to respond effectively.
- Multi-Target Coordination: With APIs, simultaneous attacks on multiple targets can be managed from a single interface, each tailored to different vulnerabilities identified through reconnaissance.
These features not only enhance the effectiveness of individual attacks but also support large-scale, coordinated campaigns that would be difficult to manage manually. Figure 1 demonstrates how API-driven interfaces make the orchestration of complex DDoS campaigns simpler for attackers.
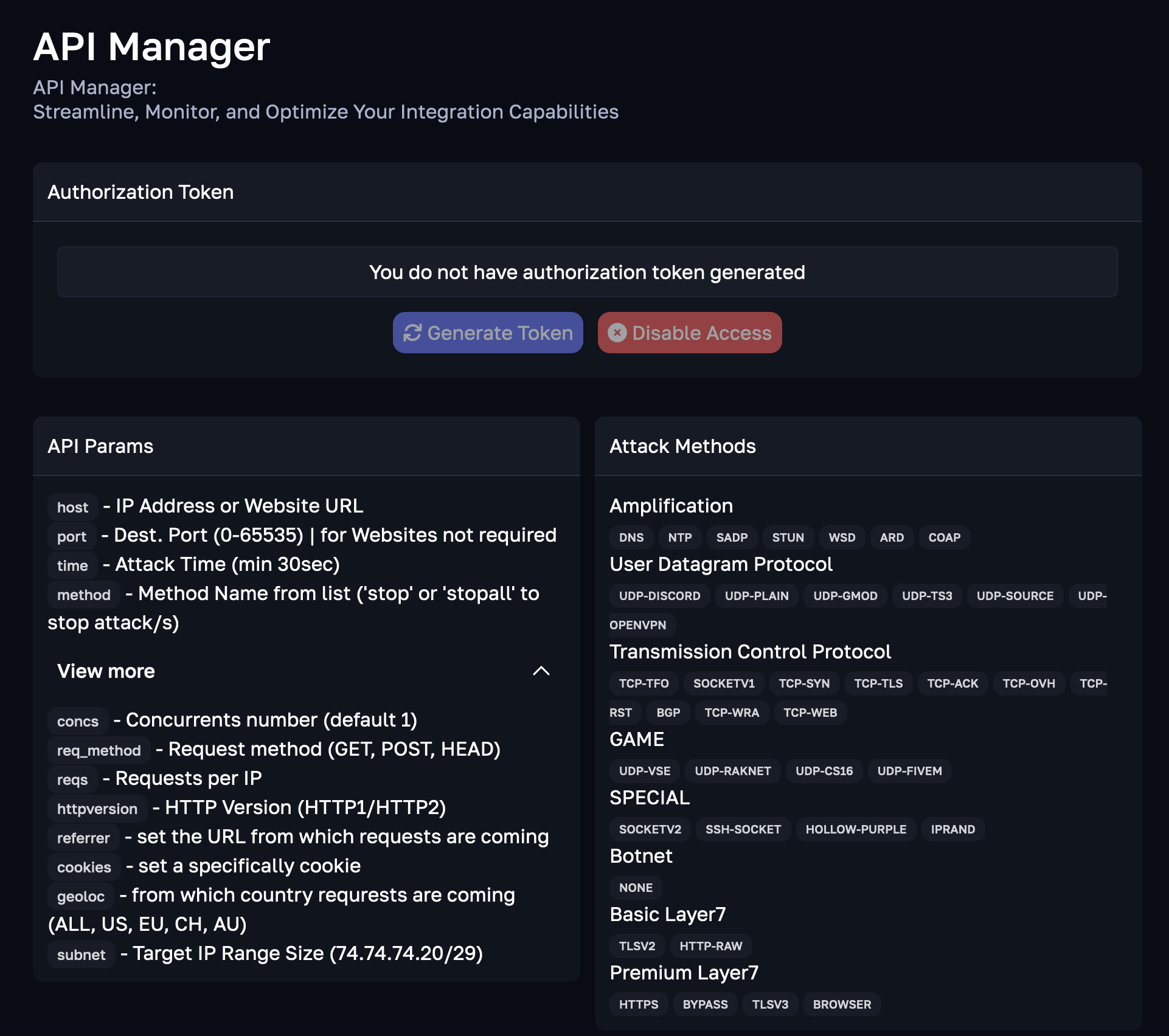
Challenges for Defenders
API-driven DDoS attacks pose unique challenges for cybersecurity teams. The speed and adaptability they provide mean that attacks can evolve rapidly. This flexibility leaves defenders scrambling to keep up, as conventional static defenses may not react quickly enough. Additionally, the seamless integration between APIs and broader hacker toolkits lowers the technical barrier, making sophisticated attacks more accessible to a wider range of cybercriminals.
Key Defensive Measures
To combat API-fueled DDoS threats, organizations should adopt a multifaceted approach:
- Implementing Adaptive Defense Systems: Solutions that can respond in real-time to changing attack patterns are essential. These systems need to go beyond basic rate-limiting and signature-based detection to offer proactive protection.
- Intelligence-Driven Insights: Access to comprehensive threat intelligence, such as that provided by NETSCOUT’s ATLAS Intelligence Feed (AIF), allows organizations to anticipate and respond to API-driven tactics.
- Monitoring for Anomalous API Activity: Understanding and monitoring traffic for signs of API-based attacks can help identify potential threats early, offering the opportunity to mitigate damage before an attack escalates.
Leveraging NETSCOUT’s Capabilities
The rise of API-driven DDoS attacks calls for advanced, adaptable defense strategies. NETSCOUT’s Adaptive DDoS Protection provides the necessary tools to detect and counteract the evolving nature of these threats. Combined with the ATLAS Intelligence Feed, organizations gain access to real-time threat intelligence that empowers them to neutralize API-originated attacks efficiently and effectively. With these tools, businesses can maintain robust defenses and stay one step ahead of sophisticated attackers leveraging API integration.
Continue reading in part four of our seven-part series: Automation (Publishing on December 12, 2024)
- Arbor Networks - DDoS Experts
- Attacks and DDoS Attacks
- DDoS Tools and Services

