- Arbor Networks - DDoS Experts
- DDoS
2024 DDoS-for-Hire Landscape Part 4
Automation

Executive Summary
Automation has become a cornerstone of modern DDoS-for-hire services, enhancing the scale and sophistication of attacks while reducing the need for continuous human oversight. This development has made it easier for attackers to deploy persistent, complex campaigns with minimal effort. In this section, we will explore how automation features are integrated into DDoS platforms, the implications for cybersecurity, and the best practices for defending against automated threats.
The Role of Automation in DDoS-for-Hire Services
Automation simplifies the process of launching and managing DDoS attacks, making it accessible to a broader range of attackers, including those with limited technical expertise. In a matter of minutes, an attacker can schedule and execute an assault, complete with customized settings that adjust based on the target’s response. This hands-off approach has reshaped the landscape of DDoS threats, increasing the frequency and impact of attacks.
Key Features of Automated DDoS Tools
DDoS-for-hire services now offer an array of automated functionalities, including:
- Attack Scheduling: Users can plan attacks to launch at specific times, targeting peak business hours or times when defenses are likely to be minimal. This capability increases the disruption potential and allows attackers to strike when the impact will be most severe.
- Dynamic Adjustment: Automation tools enable attackers to monitor the effectiveness of their attacks in real-time and adapt their strategies accordingly. For instance, if an initial wave of traffic is met with resistance, the tool can adjust packet size, type, or frequency to bypass new defensive measures.
- Repetitive Campaigns: Attackers can set up repetitive or cyclical attacks that continue for days or weeks, maintaining pressure on a target with little manual intervention.
Figure 1 illustrates an attack automation scheduler interface, showcasing how easy it is to set recurring attack parameters.
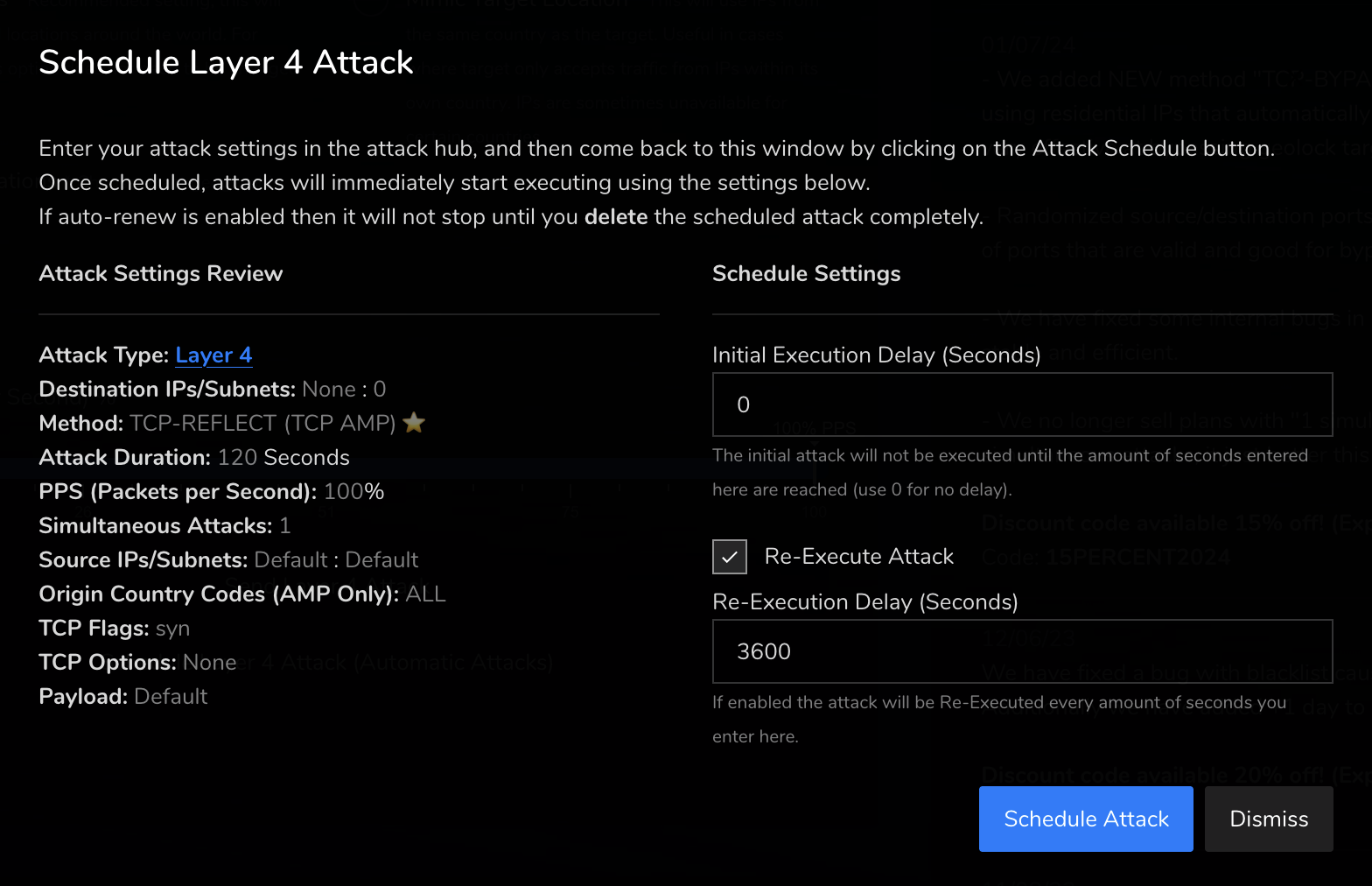
The Impact of Automation on Cybersecurity
Automation in DDoS-for-hire platforms has changed the dynamics of defending against these attacks. Security teams face challenges such as:
- Sustained Pressure on Resources: Automated attacks can keep network defenses engaged over prolonged periods, depleting resources and increasing the risk of system fatigue.
- Complex Attack Patterns: The ability to modify tactics in real-time allows attackers to deploy multi-vector strategies that require more sophisticated detection and mitigation solutions.
- Reduced Time for Response: Automation compresses the attack cycle, giving defenders less time to identify and neutralize a threat before it scales.
Case Studies of Automation in Action
One notable example of the power of automation is seen in attacks that use layer 4/7 combinations. Attackers can cycle through various types of traffic and packet structures, testing which configurations slip through defensive systems. Another case involves triggered attack waves that activate based on specific events, such as the detection of a particular user behavior or shift in network load.
Figure 2 demonstrates how real-time monitoring tools are used by attackers to tweak and re-launch automated attack waves seamlessly.
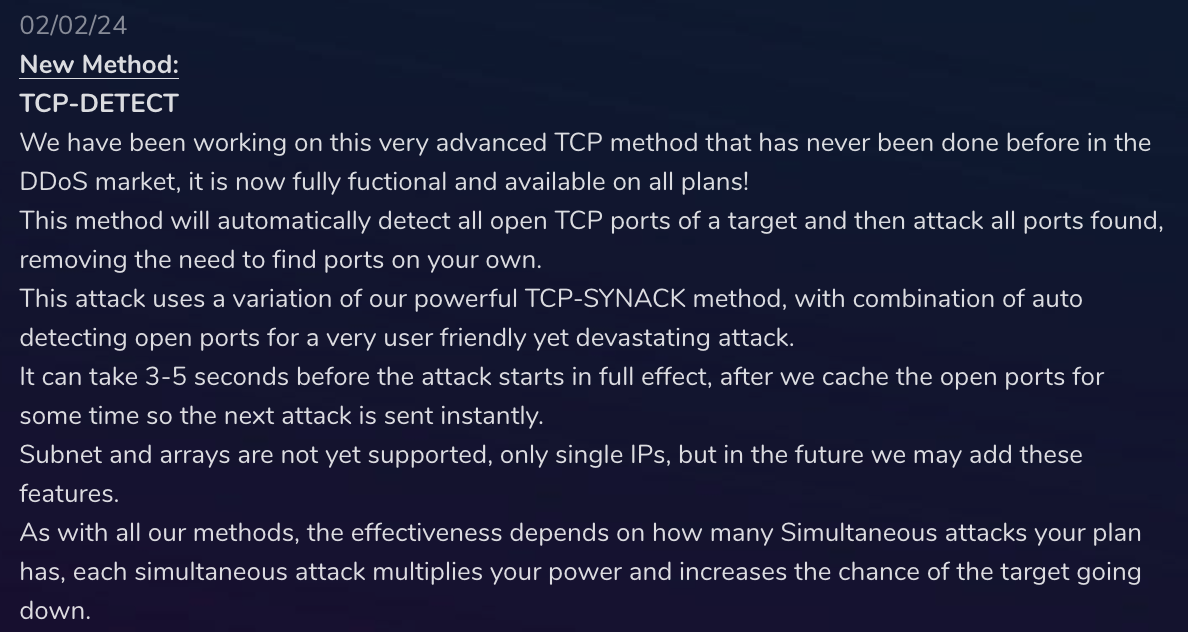
Strategies for Effective Defense
Defending against automated DDoS attacks requires a proactive approach. Key strategies include:
- Advanced Monitoring Tools: Implementing technology that can detect patterns of automated behavior, such as sudden changes in traffic that signal the start of an automated campaign.
- Adaptive Mitigation Solutions: Security measures should be capable of responding dynamically to shifting attack tactics. Solutions that integrate machine learning and real-time analytics are especially valuable for recognizing and countering these evolving threats.
- Preparedness for Prolonged Incidents: Automated DDoS campaigns can last much longer than traditional attacks. Ensuring that defenses are scalable and resilient over time is crucial for maintaining operations during prolonged attacks.
NETSCOUT’s Adaptive Response
The complexity and efficiency of automated DDoS threats call for equally dynamic defense solutions. NETSCOUT’s Automated DDoS Protection is designed to recognize and counteract these automated strategies, leveraging deep learning and real-time response capabilities to adjust to changing attack patterns. With the added support of the ATLAS Intelligence Feed, organizations benefit from up-to-date intelligence that empowers them to thwart automated DDoS campaigns effectively. This combination ensures that businesses can withstand and neutralize automated threats, safeguarding their networks from sustained and multifaceted assaults.
Continue reading in part five of our seven-part series: Infrastructure Abuse (Publishing on December 16, 2024)
- Arbor Networks - DDoS Experts
- Attacks and DDoS Attacks
- DDoS Tools and Services


