- Arbor Networks - DDoS Experts
- DDoS
2024 DDoS-for-Hire Landscape Part 5
Infrastructure Abuse

Executive Summary
Modern DDoS-for-hire platforms have evolved to include sophisticated infrastructure abuse capabilities, enabling attackers to disrupt entire networks and bypass traditional defenses. By targeting multiple assets within a network, leveraging geo-spoofing techniques, and incorporating IPv6 into their strategies, attackers have increased the complexity of defending against these threats. This section explores the types of infrastructure abuse prevalent in DDoS-for-hire services, their impact on enterprises, and the defenses needed to counteract them.
What is Infrastructure Abuse?
Infrastructure abuse in the context of DDoS-for-hire services refers to the exploitation of network resources and configuration vulnerabilities to maximize the impact of attacks. Unlike traditional DDoS attacks that target single IP addresses, infrastructure abuse tactics aim to compromise multiple elements within a network or use network misconfigurations to enhance attack effectiveness.
Techniques Used for Infrastructure Abuse
DDoS-for-hire platforms have made significant advances in infrastructure abuse methods, including:
- Carpet-Bombing Attacks: This method targets entire subnets rather than a single IP. By sending traffic across multiple IP addresses within a network, attackers create a distributed load that overwhelms defenses and increases the difficulty of mitigation.
- Geo-Spoofing: Attackers manipulate the perceived geographic origin of attack traffic, bypassing geo-blocking measures and blending in with legitimate traffic. This tactic makes it harder for defenders to filter out malicious requests without impacting genuine users.
- ISP-Spoofed Traffic: For the past few years operators have seen an increase in what appears to be attack infrastructure sourced from cloud hosting providers. Initially, these were done by more sophisticated adversaries to circumvent security measures where operators allow through trusted hosting providers. Now, this capability is a default option in most DDoS-for-hire platforms.
- IPv6 Exploitation: As IPv6 adoption grows, attackers are using its vast address space to amplify and disguise attack traffic. Some DDoS-for-hire platforms have begun integrating IPv6 attack capabilities, increasing the complexity for defenders who may not be fully prepared for this shift.
Figure 1 illustrates how an attacker can configure a DDoS campaign to target subnets, showcasing the potential scope of infrastructure abuse.
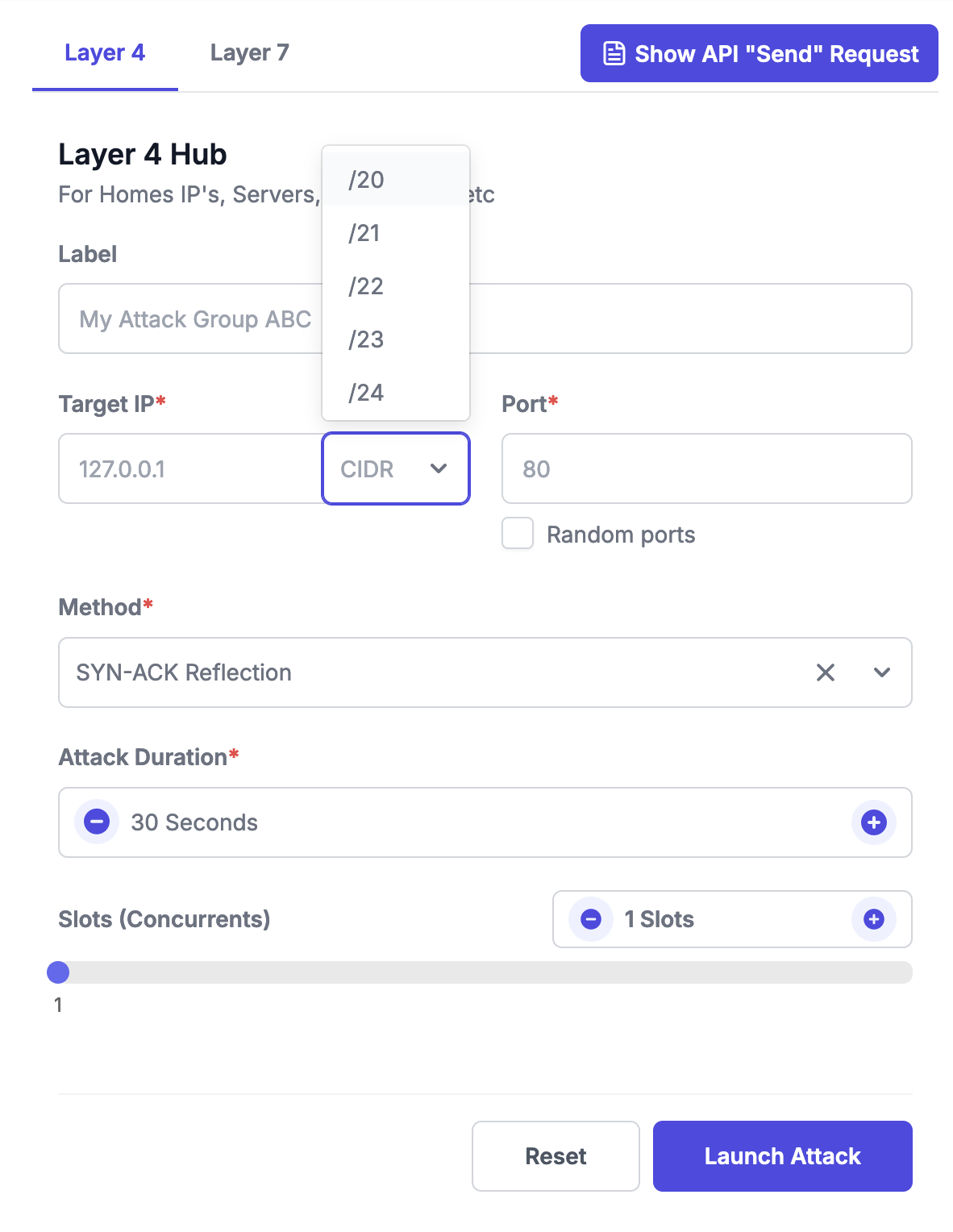
Implications for Organizations
The rise of infrastructure abuse tactics means that traditional DDoS mitigation strategies may no longer be sufficient. Enterprises face several key challenges:
- Increased Attack Surface: Targeting subnets or abusing IPv6 expands the potential attack surface, requiring broader and more comprehensive monitoring.
- Disruption of Essential Services: By using carpet-bombing or geo-spoofing, attackers can disrupt core services, affecting business operations and user trust.
- Complex Defense Requirements: Standard rate-limiting and IP blocking are ineffective against sophisticated infrastructure abuse. The dynamic nature of such attacks demands adaptive and intelligent solutions.
Real-World Examples Several recent cases illustrate the growing trend of infrastructure abuse:
- Subnetwork Overload: Organizations have reported instances where attackers targeted entire subnet ranges, overwhelming routing equipment and causing widespread outages.
- Geo-Spoofed Traffic: Businesses relying on geo-blocking as a first line of defense have been circumvented by attackers who configured their traffic to mimic that from trusted locations, complicating the differentiation between legitimate and malicious traffic.
- ISP-Spoofed Traffic: Security teams often allow trusted cloud hosting providers to connect with their services to not restrict legitimate business and user operations, but adversaries recognize this and intentionally added this feature to exploit that loophole.
- IPv6 DNS Floods: DDoS campaigns that use IPv6 query floods have been able to achieve significant amplification, affecting companies unprepared for IPv6 traffic management.
Figures 2, 3 show examples of a DDoS configuration interface with geo and hosting provider spoofing, highlighting how attackers can customize their strategies to bypass typical defensive measures.
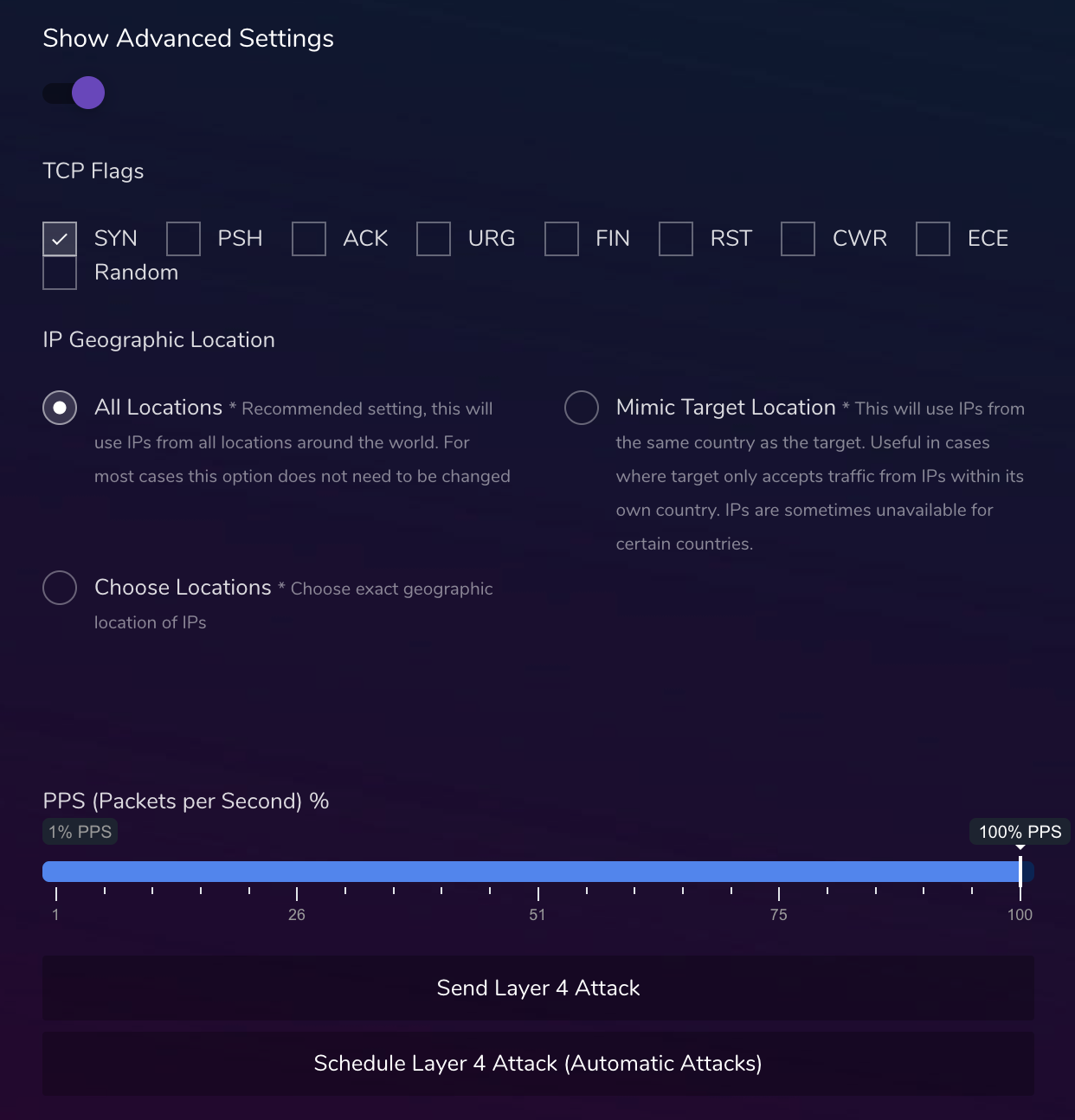
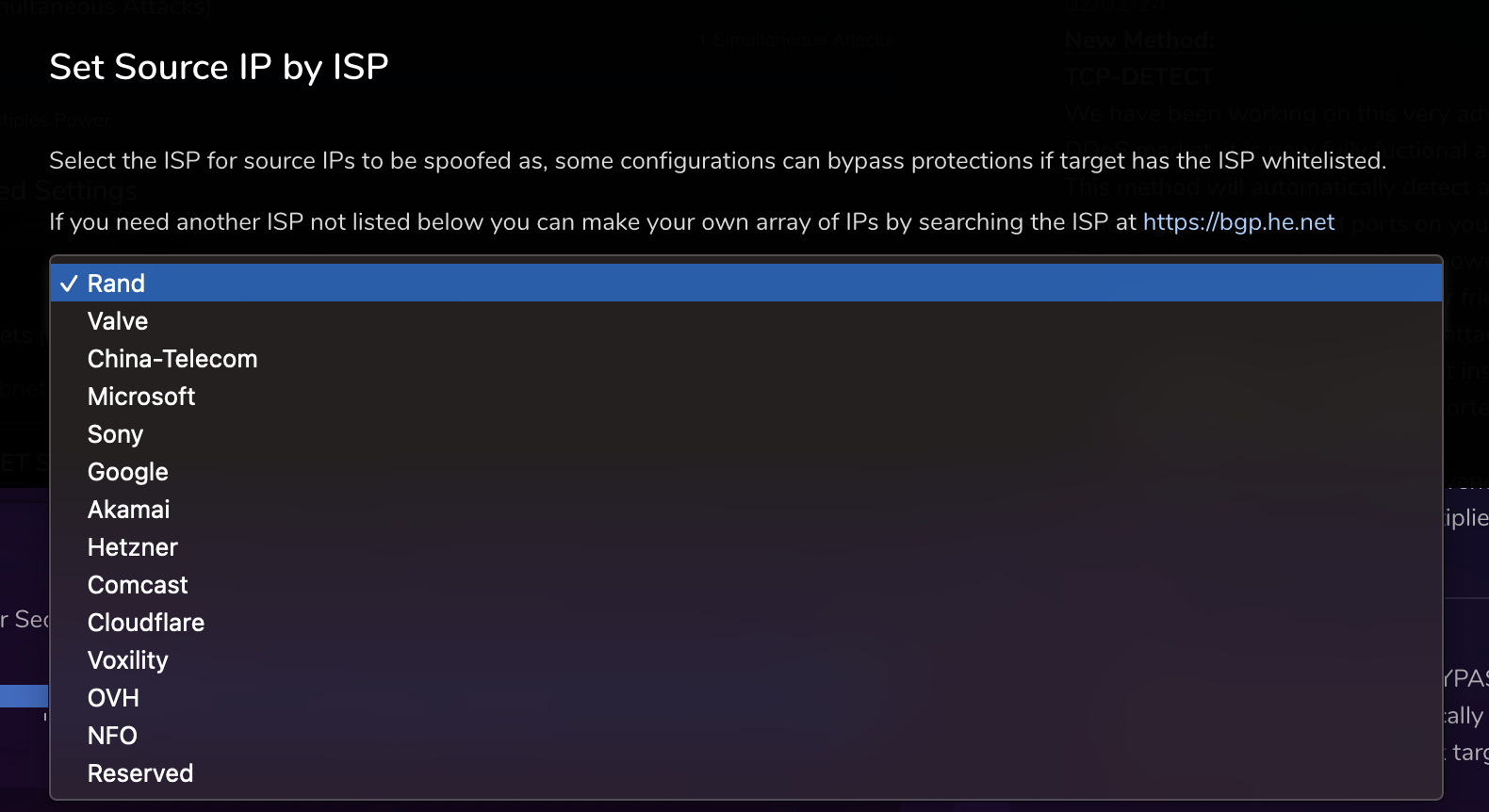
Figure 4 shows that adversaries continue to explore more attacks using IPv6 as indicated by the update to launch DNS query floods using the protocol.
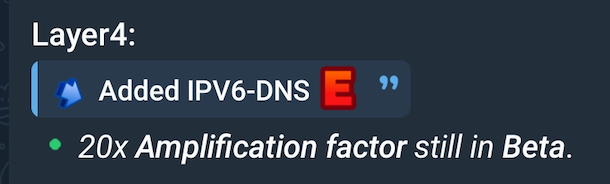
Strategic Defenses Against Infrastructure Abuse
To address the challenges posed by infrastructure abuse, organizations need to adopt advanced defense mechanisms:
- Holistic Traffic Analysis: Employ solutions that analyze traffic holistically, identifying patterns that may indicate infrastructure abuse across subnets and using behavior-based detection.
- Adaptive Threat Intelligence: Integrate real-time threat intelligence to detect new methods of attack quickly. This is especially important for keeping pace with geo-spoofing tactics and IPv6 abuse.
- Enhanced Visibility and Control: Leverage tools that provide in-depth visibility into both IPv4 and IPv6 traffic. This ensures that malicious actors cannot use the less familiar IPv6 protocol as a way to bypass monitoring.
The NETSCOUT Advantage in Infrastructure Defense
Infrastructure abuse presents a multi-dimensional challenge that traditional defenses struggle to address effectively. NETSCOUT’s Adaptive DDoS Protection, in conjunction with the ATLAS Intelligence Feed, offers organizations the necessary capabilities to monitor, detect, and mitigate infrastructure-focused attacks. With deep packet inspection, real-time analytics, and adaptive response systems, NETSCOUT equips enterprises to handle large-scale subnet targeting, geo-spoofed traffic, and IPv6-based threats, ensuring comprehensive protection against the latest DDoS strategies.
Continue reading in part six of our seven-part series: Artificial Intelligence (Publishing on December 18, 2024)
- Arbor Networks - DDoS Experts
- Attacks and DDoS Attacks
- DDoS Tools and Services


