- Arbor Networks - DDoS Experts
- DDoS
Italy in the Crosshairs
NoName056(16) Political Campaign

Executive Summary
Between February and March 2025, a series of political discussions seemingly drew the ire of multiple threat actors, including the NoName057(16). The targeting followed similar patterns of industries we’ve seen in the past, but we also highlight some additional targeting that may not have been intentional.
Activity in the Cyber Space
While ASERT primarily focuses on DDoS research, we monitor a wide range of cyber incidents by tracking publicly claimed attacks. As shown in Figure 1, reports of cyberattacks against Italian organizations spiked on February 16th, lasting for two weeks before tapering off by March 3rd.
The incidents claimed by threat actors range from website defacements, network intrusion to ransomware attacks. Yet, the most frequent claim against Italian organizations observed were DDoS attacks. ASERT observed how a large share of publicly claimed DDoS attacks between February 16 and March 03 were destined to the public sector in regional and local Italian targets.
Involvement of NoName057(16)
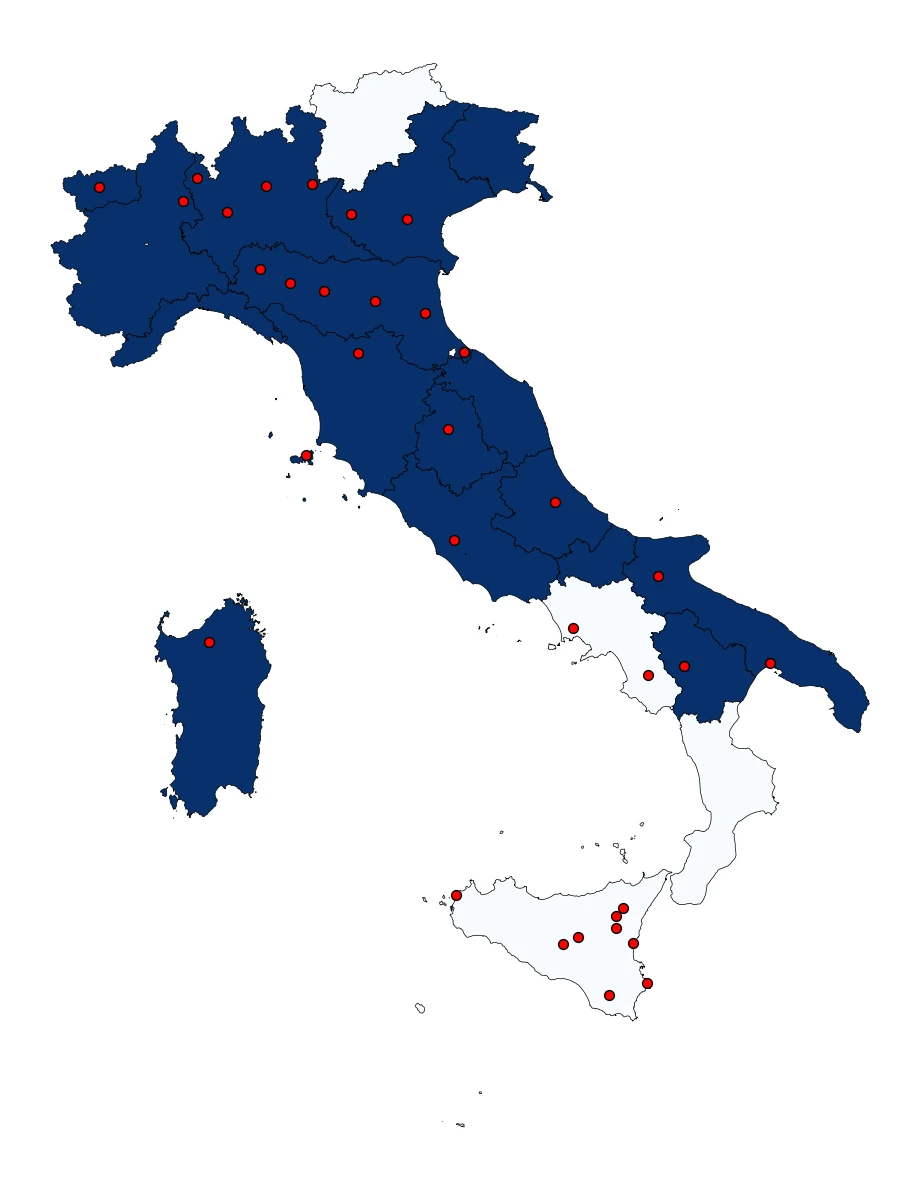
Many surges in DDoS incidents in recent years can often be tracked back to prominent DDoS hacktivist groups such as NoName057(16), whose digital traces are closely monitored by our team. Usually, the group carries out DDoS attacks through their DDoSia botnet. The action against Italy shows how the group particularly emphasizes the public sector. Figure 2 reveals how the DDoS attacks were destined to public sector organizations across the entire nation.
While there was an emphasis on the public sector, ASERT observed DDoS attacks against various industries across both the public and private sector. Figure 3 shows the frequency of how often the threat actor uses Telegram to announce responsibility for attacks. It reveals how attacks against public sector organizations are more frequently claimed as being successful.
In total, NETSCOUT observed approximately 7,000 distinct DDoS events targeting around 130 hosts. Public claims are even fewer. It becomes apparent that the number of DDoS attacks happening behind the scenes dwarf the number of officially communicated attack claims announced via the social media channels.
Intentional Targeting Automation Error?
It doesn’t take a lot of digging to assume that NoName057 potentially uses automation, as evidenced by the 130 different targets in just this recent Italian campaign. However, with automation comes common pitfalls, such as targets outside the scope of intent. Part of this campaign on Italy involved targeting firearms manufacturing organizations, but that target list included an Italian “snow gun” manufacturer, which has no apparent connection to, or involvement in actual firearms manufacturing.
Further, Initial attacks in the campaign also indicated an alphabetical approach to attacks that landed against organizations and local areas with no apparent reason or motivation. Adversaries looking to automate their attack capabilities or tools has been a growing trend the past few years to the point where nearly every facet of an attack, including choosing the DDoS attack vector, are automated.
The Big Picture
In Figure 4, ASERT illustrates the past 3 months of DDoS attacks in Italy. While the surge in cyber incidents and particularly DDoS events against Italy was significant in the short term, compared to the broader DDoS trends in the country, the changes blend with the overall growth in attacks against Italy.
Conclusion
Although there was an uptick in cyber-attack claims against Italy on social media, there is no clear evidence suggesting that the period of increased attention towards Italian organizations has had a severe impact on DDoS trends in the country. All organizations should prepare and plan to have a DDoS Protection Solution, like NETSCOUT’s Arbor DDoS, fueled by ATLAS Intelligence Feed (AIF), in place to properly defend against these waves of attacks even if they aren’t actively involved directly with industry in the crosshairs because it’s still possible to receive these attacks even if accidental in nature.
- Arbor Networks - DDoS Experts
- Attacks and DDoS Attacks
- Political DDoS