Network Security Solutions for Today's Digital Infrastructure
In today's digital economy, agility is crucial for businesses, driving significant transformations in corporate digital infrastructures. As organizations embrace cloud technologies and expand their operations across a globally distributed digital ecosystem, safeguarding this expanded threat surface requires a reinvention of security measures to protect against evolving cyber threats effectively.
Our network-based cybersecurity platform features a comprehensive portfolio of products that are designed to provide the scale, scope, and consistency required to secure today's digital infrastructure. With NETSCOUT’s Omnis Network Security solution, you can achieve security without borders, enabling your organization to stay one step ahead of cyber threats.
Our Suite of Powerful Network Security Technologies
CyberStream
Our network security sensors use patented scalable Deep Packet Inspection (DPI) technology and multiple methods of threat detection to protect your entire digital infrastructure from cyber-attacks. Long term, local storage of metadata and packets enable contextual network investigation or hunting.
Omnis Cyber Intelligence (OCI)
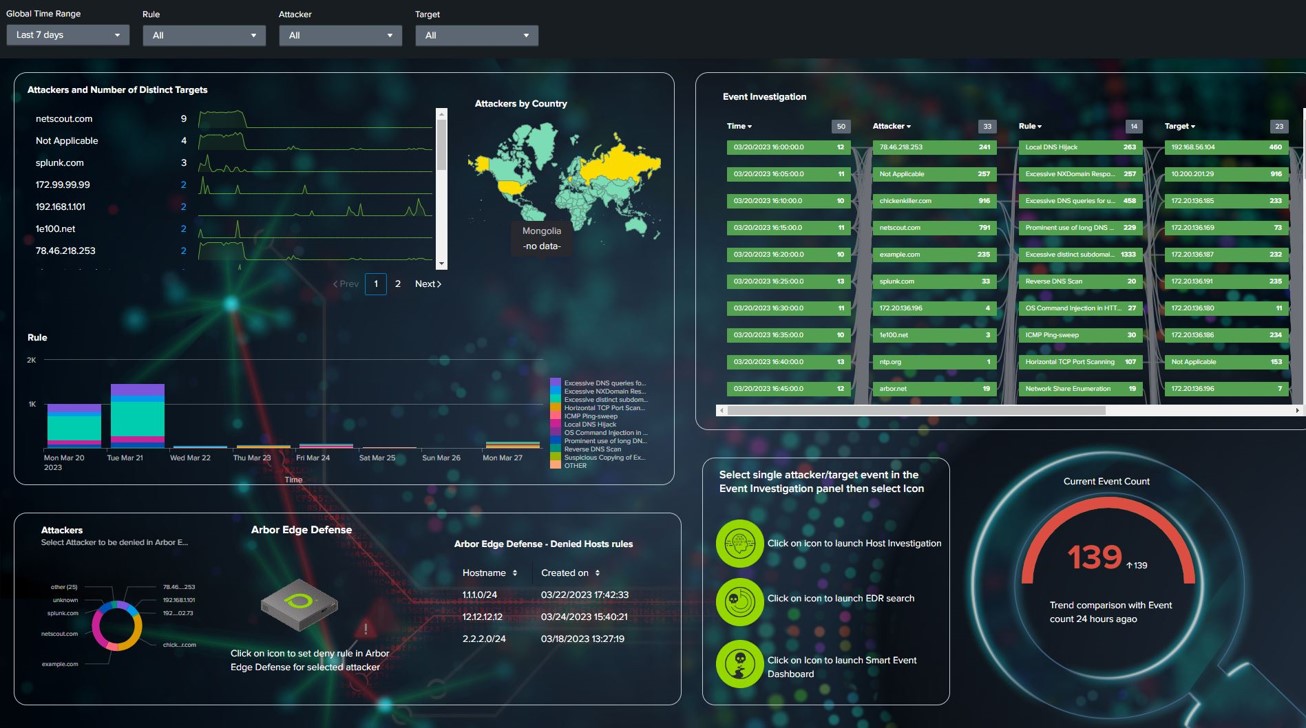
The central console for managing CyberStream sensors, OCI offers seamless management, visualization, and workflows for real-time and historical threat detection and investigation. OCI empowers you to stay proactive and respond effectively to security events.
Adaptive Service Intelligence (ASI)
Our patented technology converts raw packets into a rich source of layer 2-7 metadata called Smart Data. ASI enhances your network's intelligence, enabling accurate and efficient threat detection.
ASI Flow
ASI Flow-based behavioral analysis uses ML to create deterministic signatures, resulting in fewer false positives. This allows for precise threat identification, minimizing unnecessary alerts, and improving efficiency.
ATLAS Intelligence Feed (AIF)
A global threat intelligence feed covering over 50% of all internet traffic across 190 countries. AIF keeps you informed about emerging threats and provides valuable insights to bolster your security strategy.
nGenius Decryption Appliance (nDA)
Offering high-performance visibility into encrypted traffic, including TLS/SSL and SSH. With flexible deployment options, nDA ensures optimal performance of downstream service and security assurance tools.
Omnis AI Streamer
Exporting patented ASI data to a data lake, Omnis AI Streamer allows you to combine it with other data sources for custom analysis. This helps you gain deeper insights into your network's security posture and make informed decisions.
Arbor Edge Defense (AED)
Acting as the first and last line of smart, automated perimeter defense in your network, AED blocks inbound DDoS attacks, cyber threats, and outbound Indicators of Compromise, providing robust protection for your organization.
Comprehensive Network Security and Visibility Solutions
At NETSCOUT, we understand the importance of a comprehensive solution for network security and visibility. That’s why our CyberStream and vSTREAM platforms, powered by Adaptive Service Intelligence (ASI) technology, offer unparalleled visibility without borders. This level of visibility enables security without borders, ensuring your network remains protected across your entire digital infrastructure.
Multidimensional Threat Detection
Our multidimensional threat detection capabilities provide real-time security using targeted machine learning techniques. By utilizing a combination of IoCs, policies, signatures, unexpected traffic, and behavior analysis, we ensure comprehensive security coverage while minimizing false positives.
Investigation and Threat Hunting
For historical investigation and proactive cyber threat hunting, our Omnis Cyber Intelligence central console offers comprehensive capabilities, allowing you to effectively manage security events, conduct investigations, and perform historical analytics in a single NDR platform.
Security Ecosystem Integration
Integration is key in today's complex cybersecurity landscape. Our solutions seamlessly integrate with other cybersecurity tools, including SIEM, EDR, SOAR, and XDR systems. With tri-directional integration, we enhance workflows, collaboration, and response times, enabling faster incident detection and response. Additionally, our patented Smart Data can be exported into any third-party data lake for further analysis and correlation.
Smart Edge Protection
Detection is not enough. After a threat has been detected and confirmed with Omnis Cyber Intelligence, it can issue a blocking policy in network edge devices, such as a firewall or our own Arbor Edge Defense (AED), to stop the threat before further impact occurs.
Award Winning Advanced NDR
“NETSCOUT’s unique ASI technology allows companies to truly unlock the actionable intelligence embedded in network transactions and packets,” said Christopher Kissel, research director, security and trust products, IDC. “Where others have failed, NETSCOUT has made the use of packet data fast and affordable with their patented metadata extraction, intelligent reduction, and indexing. Omnis Cyber Intelligence provides security analysts with the information they need to quickly and accurately assess the scope and scale of an incident and reduce the associated risk and negative impact.”
- Chris Kissel, Research Director, Security & Trust Products, IDC


2024 Business Technology Winner
Best Advancement in Cybersecurity

2022 Fortress Cybersecurity Awards
Threat Detection Category Winner

2022 Global Infosec Awards
Network Detection and Response Category Winner
2024 Business Technology Winner, Best Advancement in Cybersecurity
2022 Fortress Cybersecurity Awards, Threat Detection Category Winner
2022 Global Infosec Awards, Network Detection and Response Category Winner
The Netscout Omnis Network Security Solution






