- What Does Threat Hunting Accomplish?
- What Does Threat Hunting Accomplish?
- Difference Between SOC and Threat Hunting
- MITRE ATT&CK and Threat Hunting
- How OCI Helps

Robert Derby
Senior Product Marketing Manager
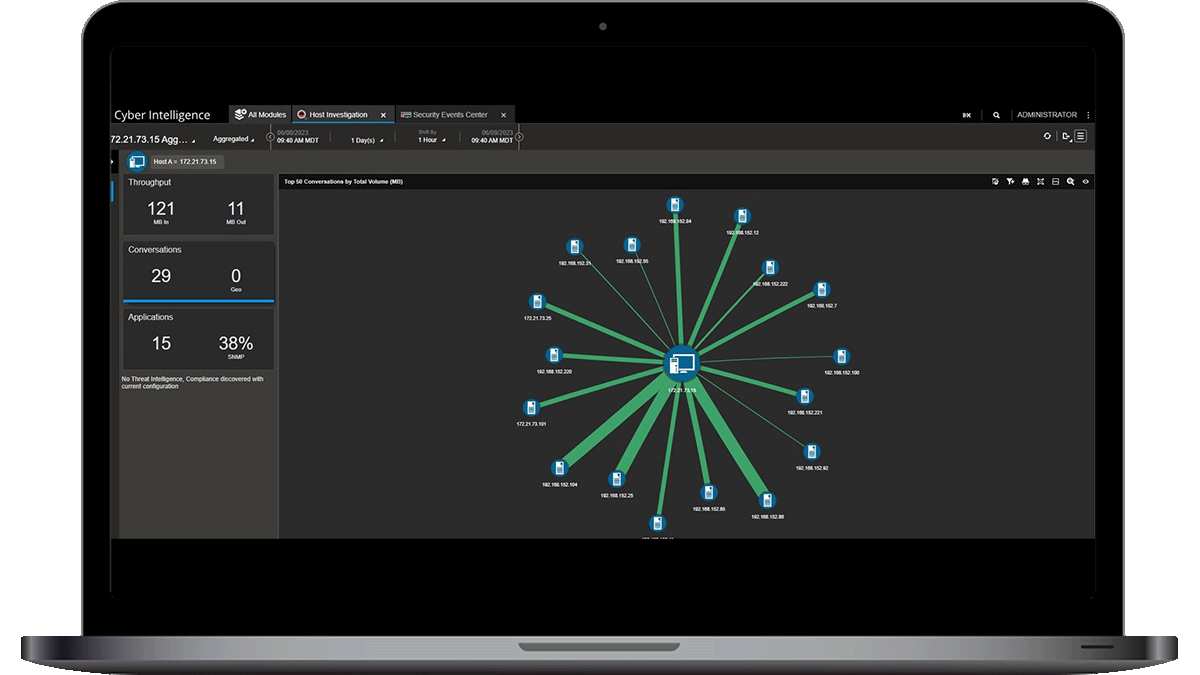
What is Threat Hunting?
Cyberthreat Hunting is a proactive cybersecurity approach that involves actively searching for and mitigating potential threats within a network. It goes beyond traditional security measures by seeking out anomalies and vulnerabilities before they escalate into significant incidents.
In today's dynamic digital landscape, where cyber adversaries constantly evolve tactics, NETSCOUT's Omnis Cyber Intelligence (OCI) and Omnis CyberStream play a pivotal role. Forming a comprehensive platform for Advanced Network Threat Detection and Response based on Deep Packet Inspection (DPI), they provide real-time visibility, behavioral analytics, and seamless scalability. This proactive strategy enhances overall security by complementing traditional security measures and ensuring organizations stay ahead of emerging threats.
What does Threat Hunting Accomplish in Cybersecurity?
Threat hunting in cybersecurity is a proactive strategy focused on identifying and eliminating potential threats before they escalate. This approach involves ongoing monitoring and analysis of network activities to detect anomalies and potential risks that might go unnoticed by traditional security measures. NETSCOUT's network detection and response (NDR) solution, Omnis Cyber Intelligence (OCI), elevates threat hunting by offering real-time visibility into network traffic, leveraging advanced threat intelligence, and providing scalability and adaptability to keep pace with evolving digital landscapes.
OCI's real-time visibility ensures that security teams can promptly detect abnormal patterns or behaviors, allowing for swift response to potential threats. The integration of advanced threat intelligence, such as ASI, enriches the data with contextual information, enhancing the understanding of potential risks. Moreover, OCI's scalability and adaptability enable organizations to effectively hunt for threats in a rapidly changing network environment, reinforcing the proactive nature of threat hunting in cybersecurity.
What is the Difference Between a SOC and Threat Hunting?
In simple terms, SOC = Reactive and Threat Hunting = Proactive
In the realm of cybersecurity, the distinction between a Security Operations Center (SOC) and threat hunting lies in their primary functions and approaches. A SOC operates reactively, focusing on monitoring and responding to security incidents as they occur. Its role is crucial for incident response, incident detection, and ensuring the overall security posture. Conversely, threat hunting represents a proactive and dynamic strategy that actively seeks out potential threats before they manifest into security incidents.
NETSCOUT's Omnis Cyber Intelligence (OCI) exemplifies the proactive nature of threat hunting. While a SOC responds to known incidents, OCI, through threat hunting, anticipates and mitigates potential threats. OCI's real-time visibility, advanced threat intelligence integration, and scalability empower organizations to actively seek out anomalies and vulnerabilities, contributing to a more robust cybersecurity defense. This proactive approach aligns with the evolving landscape of cybersecurity threats, where anticipating and neutralizing threats before they become critical is essential for maintaining a secure digital environment.
Can you use frameworks such as MITRE ATT&CK for threat hunting?
Yes, utilizing the MITRE ATT&CK framework for threat hunting provides a structured and comprehensive approach to identify and mitigate potential cyberthreats. Threat hunters can leverage MITRE ATT&CK's detailed mapping of adversarial tactics, techniques, and procedures (TTPs) to enhance their understanding of potential threat scenarios. By aligning their hunting strategies with known TTPs, security teams can proactively search for indicators of compromise within their network.
NETSCOUT's Omnis Cyber Intelligence (OCI) enhances the effectiveness of threat hunting by seamlessly integrating with the MITRE ATT&CK framework. OCI provides real-time visibility into network activities and leverages advanced threat intelligence to identify anomalies aligned with known TTPs. The platform's scalability and adaptability ensure that organizations can stay ahead of emerging threats by continuously updating their threat hunting strategies based on the evolving landscape. OCI's collaborative features streamline workflows, enabling security teams to efficiently investigate and respond to potential threats identified through the MITRE ATT&CK framework. By combining the structured approach of MITRE ATT&CK with OCI's proactive capabilities, organizations can fortify their cybersecurity defenses and stay resilient in the face of evolving cyberthreats.
How Does OCI Assist in Cyberthreat Hunting?
NETSCOUT's Omnis Cyber Intelligence is designed to address the challenges posed by the evolving threat landscape. OCI offers comprehensive visibility, proactive threat detection, and collaboration among security analysts. OCI doesn't just wait for threats to manifest; it actively alerts on potential risks, ensuring administrators are aware before any damage potentially occurs. By leveraging machine learning and advanced threat intelligence, OCI provides a dynamic and reliable defense against the ever-changing tactics of cyber adversaries.
If you are looking to solve the problems associated with traditional threat hunting methods and enhance your cybersecurity posture, implementing NETSCOUT's Omnis Cyber Intelligence is a significant step forward. Explore our solution page for more information on how OCI can transform your threat hunting capabilities.
